Passwords typically suffer from one or more of the following problems: They are not complex enough, they are difficult to remember, or they are saved in a far too insecure way. Although admins are supposed to use a separate, strong password for each IT system, many don't, and they write down their credentials somewhere they can be easily found; the classic worst case is a sticky note on the monitor. Passwords pose a challenge, not only for the user, but also for admins. For example, you can never be sure whether the password used was entered by the legitimate user or by someone else (e.g., a cybercriminal or bot).
Microsoft, Google, and Apple are now tackling the problem. Google and Apple unveiled the passkey method at their developer conferences to enable passwordless logins with cryptographic keys, making the classic password obsolete.
The Eternal Cat-and-Mouse Game
IT security is not a purely technical challenge but, instead, a human one. However, people should not to be considered the problem or the weakest link. Instead, as it turns out, they are simply the preferred attack vector today. Problems such as phishing, wherein crooks lure the user to a fake website to grab credentials, can always lead to nasty surprises.
IT has therefore continuously invented new and different strategies to reduce the likelihood of users falling victim to an attacker. For example, two-factor authentication (2FA) is a widely implemented approach. It involves a combination of various factors such as knowledge (e.g., password, PIN) and possession (e.g., a transaction authentication number (TAN) generator, an authenticator app) supported by biometrics (e.g., fingerprint). However, even these strategies do not ensure complete security. Attackers have learned how to outsmart both users and IT systems. This cat-and-mouse game goes on wherever you look.
How Passkeys Work
The passkey process is based on the Web Authentication API (WebAuthn), a core component of the FIDO (fast identity online) Alliance's FIDO2 specifications, and is intended to improve the user experience. It is also committed to making security issues such as weak credentials, lost credentials, and phishing impossible. A passkey is based on public and private keys. When a user registers on a website or with an app, the operating system creates a unique cryptographic key pair in the background for the app user account or website.
The end user's device itself generates these keys and transmits the first key, which is the public key, to the remote IT system. As with any private-public key method, this public key is not a secret. It doesn't matter if it is intercepted or stolen from the IT system by some criminal; however, the second key generated is private and is appended to the password manager on Android or the iCloud Keychain on iOS. An external system never learns what the private key is.
The device protects access to this key with the maximum available security. If biometric sensors are present on the device, they can be used to gain access. If this is not the case, the device password is required.
Thanks to passkeys, users no longer need to enter a password to log in to apps and websites. Once generated, any login to an IT system from now on will proceed as follows (Figure 1):
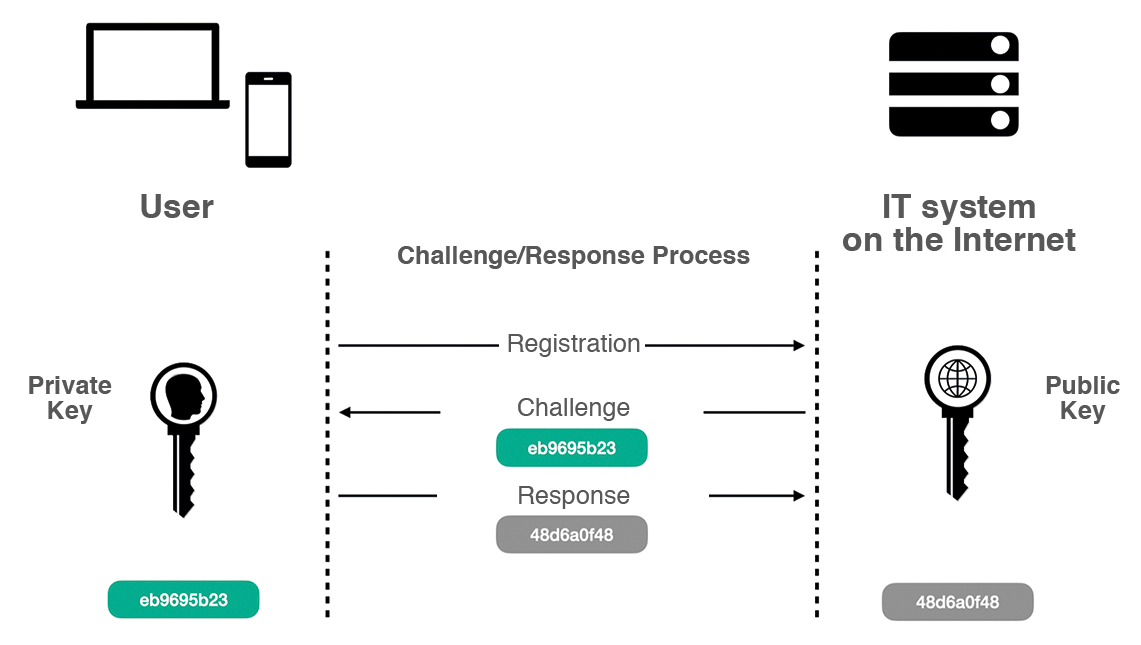
- The server sends a one-time challenge to the device. This is a buffer of cryptographically random bytes generated by the server to prevent replay attacks. Even though WebAuthn offers various challenge-response algorithms, the Apple platform uses the AES256 standard because of the longer key length.
- Only the private key on the user's own terminal device is capable of generating a valid response for the challenge (i.e., for the user's login). The device generates the response -- a signature -- internally and sends it back to the server.
- The server then validates the response with the public key it already has.
- Once the response provided by the device is validated, the user is considered to be logged in.
Although this sounds complicated, it all takes place under the hood. The user only has to navigate through simple login screens.
Advantages and Disadvantages of Passkeys
Passwordless authentication makes it impossible to sniff login data and reliably prevents data theft. In a corporate environment, you will want to support this standard to the maximum. You will certainly encounter attempts to attack individual devices to gain access to IT system accounts, but these are always targeted, sophisticated attacks with different approaches. Stealing passwords is far easier and more scalable than stealing devices and exploiting their digital content.
Integration on the vendor side is very easy and possible without any massive overhead for existing software architectures. However, the passkey method also has potential disadvantages that users need to be aware of. As mentioned, the passkey is generated on the device that is used for the login. For Apple, passkeys are automatically synchronized with all of the user's other Apple devices running under the same Apple ID. However, because passkeys are based on the FIDO standard, which is also implemented on Android and Windows, there is a way to log in on a device that is not part of the Apple ecosystem.
The third-party device generates a QR code when logging in. The authorized device (i.e., one with a passkey) needs to scan this, which grants access on the third-party device. Strictly speaking, however, scanning is not the whole truth, because the system uses Bluetooth LE, among other things, to check whether the authorizing device is nearby. This technique makes phishing attacks with the use of third-party systems far more difficult. Sending a QR code by email for a potential victim to scan will no longer work.
Sending passkeys to friendly Apple devices can also be done with AirDrop, allowing other computers to be permanently authorized for the account in question. However, these computers can now also legitimize other third-party devices. Because passkeys, in contrast to passwords, do not expire and must therefore be reassigned after a certain period of time, this almost unlimited transfer of the authorization function should be seen as a disadvantage from a security perspective.
Although a passkey can easily be used within an ecosystem (e.g., a password manager on Android or the iCloud Keychain on iOS), another critical consideration crops up. Passkey users depend on the functionality of their Google or Apple accounts. For example, if an Apple account is blocked, access to online resources is generally lost. Therefore, you should store a recovery contact in case your devices or computers become completely unusable.
Conclusions
By implementing the passkey process, Apple and other major manufacturers are taking a major step toward replacing passwords. Presumably passkeys will become established in many areas. The convenience of being able to synchronize passkeys between your devices makes access easier. In theory, at least, this means that users can access arbitrary data at any time, from any location, with any device. At the same time, however, sharing passkeys with third parties is still one of the challenges that vendors need to address. Finally, the dependence on a platform ecosystem is a difficult concept to sell.
This article originally appeared in ADMIN magazine and is reprinted here with permission.
Want to read more? Check out the latest edition of ADMIN Network & Security.








Comments